In this tutorial, we will demonstrate how to perform a directory brute force attack using two powerful tools: Gobuster and Dirb. We will apply these tools to the website dir.cyberfarm.fun to discover hidden directories like /admin-***** and files such as .txt files that could contain sensitive information.
What is Directory Brute Forcing?
Directory brute forcing is the process of attempting to find hidden directories or files on a web server by systematically trying different names or patterns. It's a common technique used by penetration testers and attackers to locate sensitive files or admin panels that are not linked directly on the website.
In this tutorial, we will use Gobuster and Dirb to perform brute force attacks to find hidden directories and files.
Tools Required
- Gobuster: A fast directory/file brute force tool written in Go. It supports HTTP and DNS modes and can discover directories and files by using a wordlist.
- Dirb: Another popular directory brute force tool that works by trying different directory and file names using a wordlist.
- Downloading the directory wordlist to brute force from https://dir.cyberfarm.fun/res/dir.txt
We will demonstrate both tools and show how they can be used on dir.cyberfarm.fun to find hidden directories such as /admin-*****.
1. Using Gobuster for Directory Brute Forcing
What is Gobuster?
Gobuster is a tool written in Go that is used for brute-forcing directories and files in web applications. It can be used to discover hidden directories, files, and even virtual hosts.
Installation of Gobuster
You can install Gobuster on Kali Linux or any other Linux distribution using the following command:
sudo apt install gobuster
Basic Gobuster Command
To begin brute-forcing directories on dir.cyberfarm.fun, use the following command:
gobuster dir -u https://dir.cyberfarm.fun -w /path/to/dir.txt
- -u: The URL of the website you are attacking.
- -w: The path to your wordlist file containing common directory names.
Looking for Specific File Extensions
Gobuster can also be used to brute-force specific file extensions (e.g., .txt, .php). This is useful when you want to find hidden files like admin.txt or config.php.
To search for .txt and .php files in addition to directories, use the -x flag:
gobuster dir -u https://dir.cyberfarm.fun -w /path/to/wordlist.txt -x txt,php
This command will search for directories and files with .txt and .php extensions.
Example Command for Brute Forcing Directories
Let’s say you want to find hidden directories and files in dir.cyberfarm.fun using the SecLists wordlist (which contains many common directory and file names). You can run the following command:
gobuster dir -u https://dir.cyberfarm.fun -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,phpThis will try every word in the directory-list-2.3-medium.txt wordlist and append .txt and .php to each word to check for file existence.
What to Look For
- Hidden directories such as
/admin-panel. - Files like
login.txt,config.php, and other sensitive files that may contain security information.
2. Using Dirb for Directory Brute Forcing
What is Dirb?
Dirb is a simple command-line tool for brute-forcing directories and files. It uses a wordlist to try different directory and file names and can be particularly useful for quickly discovering hidden resources on a web server.
Installation of Dirb
To install Dirb on Kali Linux or any other Linux system, use the following command:
sudo apt install dirb
Basic Dirb Command
To start a directory brute-force scan on dir.cyberfarm.fun using Dirb, use the following command:
dirb https://dir.cyberfarm.fun /path/to/wordlist.txt
- http://dir.cyberfarm.fun: The URL of the site you want to scan.
- /path/to/wordlist.txt: The path to the wordlist that will be used to guess directories and file names.
Using Dirb with a Common Wordlist
Dirb comes with a default wordlist, but you can also use custom wordlists, such as the SecLists wordlist for directory brute forcing. For example:
dirb http://dir.cyberfarm.fun /usr/share/dirb/wordlists/big.txt
This command will use the big.txt wordlist to try various common directories and files.
Looking for Specific File Extensions
To search for specific file extensions, you can pass the -X option to Dirb. For example, to search for .txt and .php files:
dirb http://dir.cyberfarm.fun /path/to/wordlist.txt -X .txt,.php
This will try to discover directories and .txt, .php files at the same time.
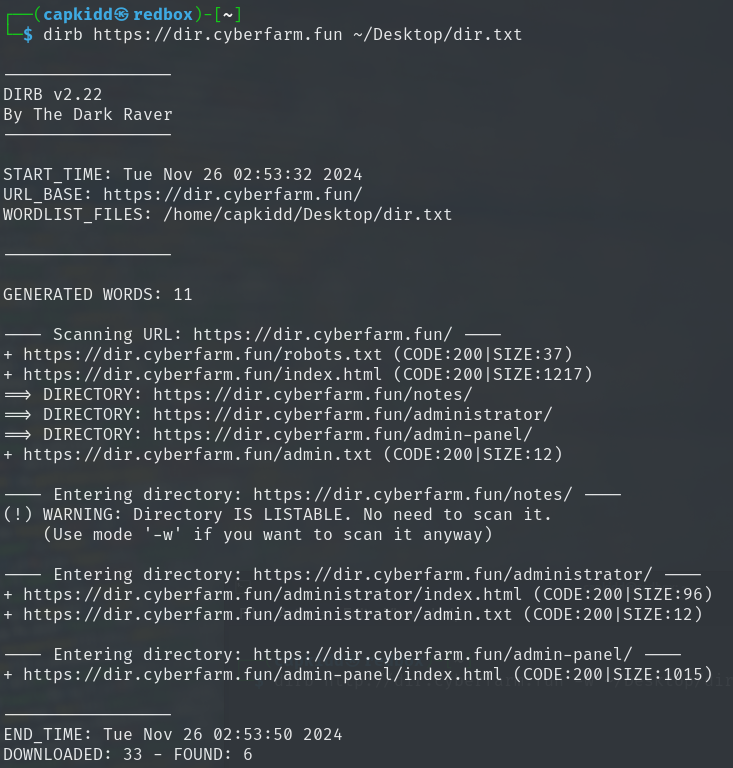
3. Performing the Directory Brute Force on dir.cyberfarm.fun
Start the Attack
We can now use both tools to find the hidden /admin-panel directory on dir.cyberfarm.fun.
Using Gobuster:
gobuster dir -u https://dir.cyberfarm.fun -w /path/to/wordlists/dir.txt -x txt,php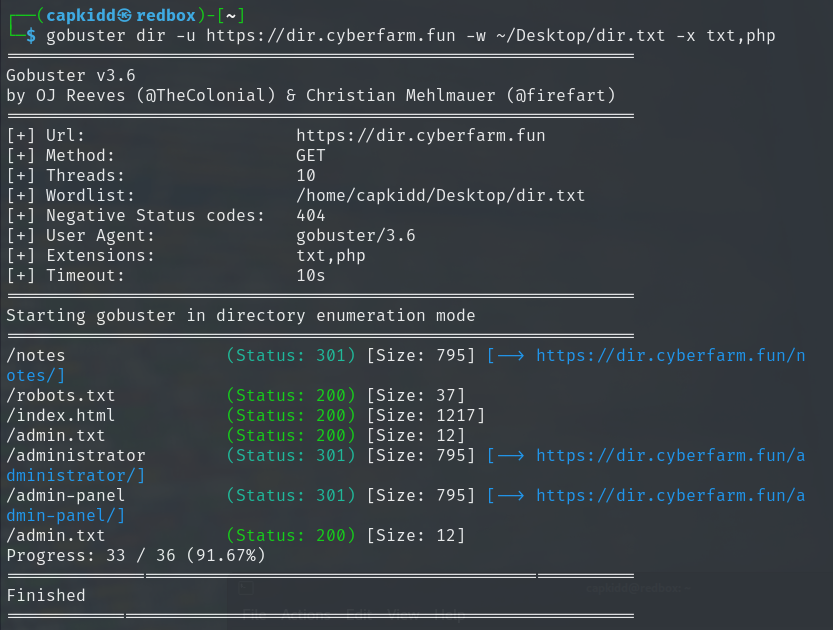
Using Dirb:
dirb https://dir.cyberfarm.fun /path/to/wordlist/dir.txt
Both tools will start making requests to the server and report back any directories or files they find based on the wordlist and extensions provided.
5. Conclusion
In this tutorial, we've demonstrated how to use Gobuster and Dirb for directory brute forcing on dir.cyberfarm.fun. By using these tools with the right wordlists and file extensions, we were able to find hidden directories and files that are not directly linked on the website. These techniques are valuable for penetration testers and security researchers looking to uncover hidden resources in web applications.
