URL: https://sql-injection.cyberfarm.fun/index.html
In this walkthrough, we'll explore a vulnerable SQL injection login panel and demonstrate how attackers exploit it to bypass authentication. This tutorial is for educational purposes only—always use this knowledge ethically and legally.
1. Understanding SQL Injection
SQL Injection is a web security vulnerability that allows attackers to interfere with the queries an application makes to its database. By manipulating input fields, attackers can bypass authentication, retrieve sensitive data, or even modify database contents.
2. Setting Up the Environment
- URL: Access the login page at https://sql-injection.cyberfarm.fun/index.html.
- Target: A login form that asks for a username and password.
- Goal: Bypass login authentication using SQL Injection.
3. Exploring the Login Form
Normal Input
- Open the URL and enter valid credentials:
- Username:
admin - Password:
password123
- Username:
- On successful login, you are redirected to the dashboard.
Testing out the login with the provided username and password and its successful we have been redirected to the dashboard.
4. Exploiting SQL Injection
Vulnerable Query
The backend executes the following SQL query when processing the login form:
SELECT * FROM users WHERE username = '$user' AND password = '$pass';By injecting malicious input into the username field, we can manipulate this query.
Injection Payload
Enter the following:
- Username:
' OR '1'='1' -- - Password: (Leave blank or type anything)
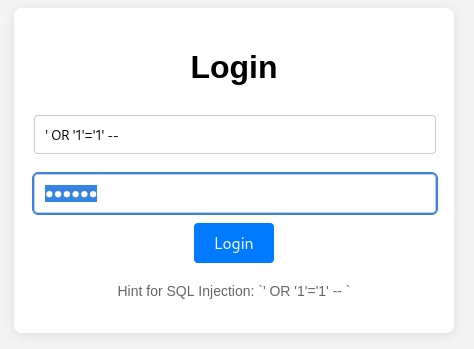
How It Works
The payload modifies the query to:
SELECT * FROM users WHERE username = '' OR '1'='1' -- AND password = '';
- The
OR '1'='1'condition is always true. - The
--comments out the rest of the query, bypassing the password check.
5. Demonstrating the Exploit
- Open the login form.
- Enter:
- Username:
' OR '1'='1' -- - Password: (Leave blank)
- Username:
- Click Login.
- You are redirected to the dashboard without valid credentials.
- make sure when you insert the sql injection leave a space after the "-- "
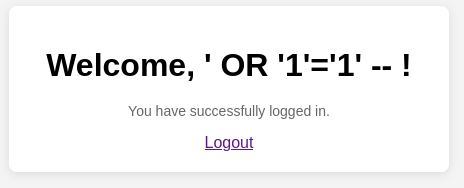
6. Observing the Results
After a successful SQL Injection:
- The dashboard displays a welcome message, showing the injected input as the logged-in user.
- This demonstrates how SQL Injection allows unauthorized access.
7. Preventing SQL Injection
Explain why this vulnerability exists and how to mitigate it:
Prepared Statements: Use parameterized queries to prevent SQL Injection. Example in PHP:
$stmt = $conn->prepare("SELECT * FROM users WHERE username = ? AND password = ?");
$stmt->bind_param("ss", $user, $pass);
$stmt->execute();- Input Validation: Sanitize user input to block malicious characters.
- Principle of Least Privilege: Limit database user permissions to prevent destructive queries.
- Monitoring and Logging: Detect unusual query patterns to identify potential attacks.
8. Conclusion
This demonstration shows how simple SQL Injection attacks can bypass authentication and compromise systems. By understanding how these attacks work, developers can take steps to secure their applications and databases effectively.
Always remember to:
- Educate yourself ethically.
- Never perform unauthorized tests.
For more tutorials on cybersecurity, visit CyberFarm.Fun!
